CSC 429: Computer Security
CSC 429
Semester: First semester 1447H - Fall 2025
Course title: Computer Security
Credit hours: 3
Instructor: Dr. Iehab AL Rassan irassan@ksu.edu.sa
Office: 2179
Office Phone: 467-6585
E-mail: irassan@ksu.edu.sa
Office Hours: Monday 1 P.M –2 P.M, (This might change – always check my home page first)
Course website :Section1 (10 AM to 12) : https://piazza.com/ksu.edu.sa/spring2026/csc429sec1/home
Course website :Section1 (1 PM to 3 PM) : https://piazza.com/ksu.edu.sa/spring2026/csc429sec2/home
Course Objectives
The objective of this course is to provide the fundamentals of theories and methods
of computer security including maintaining confidentiality, availability and
integrity, threat and vulnerabilities. In addition, it introduces method of public-key
encryption, symmetric encryption, access control, user authentication, security
policy, risk assessments, network security, operating system security, and intrusion
detection systems.
Pre-requisites
CSC 329: Computer Networks
Main Textbooks
[1] Computer Security: Principles and Practice, W. Stallings and L. Brown, 4th
Edition, 2017, ISBN-13: 978-0134794105.
Additional Textbooks
[2] Introduction to Cryptography and Network Security, Behrouz A. Forouzan,
ISBN-13 9780073327532, McGraw-Hill Forouzan networking series
[3] Introduction to Computer Security, Matt Bishop, 1st Edition, 2004, ISBN-
13: 978-0321247445.
[4] Security Engineering: A Guide to Building Dependable Distributed Systems,
Ross J. Anderson ,3rd Edition, 2020, ISBN-13: 978-1119642787.
[5] Principles of Information Security, M. Whitman and H. Mattord, 6th Edition,
2017, ISBN-13: 978-1337102063.
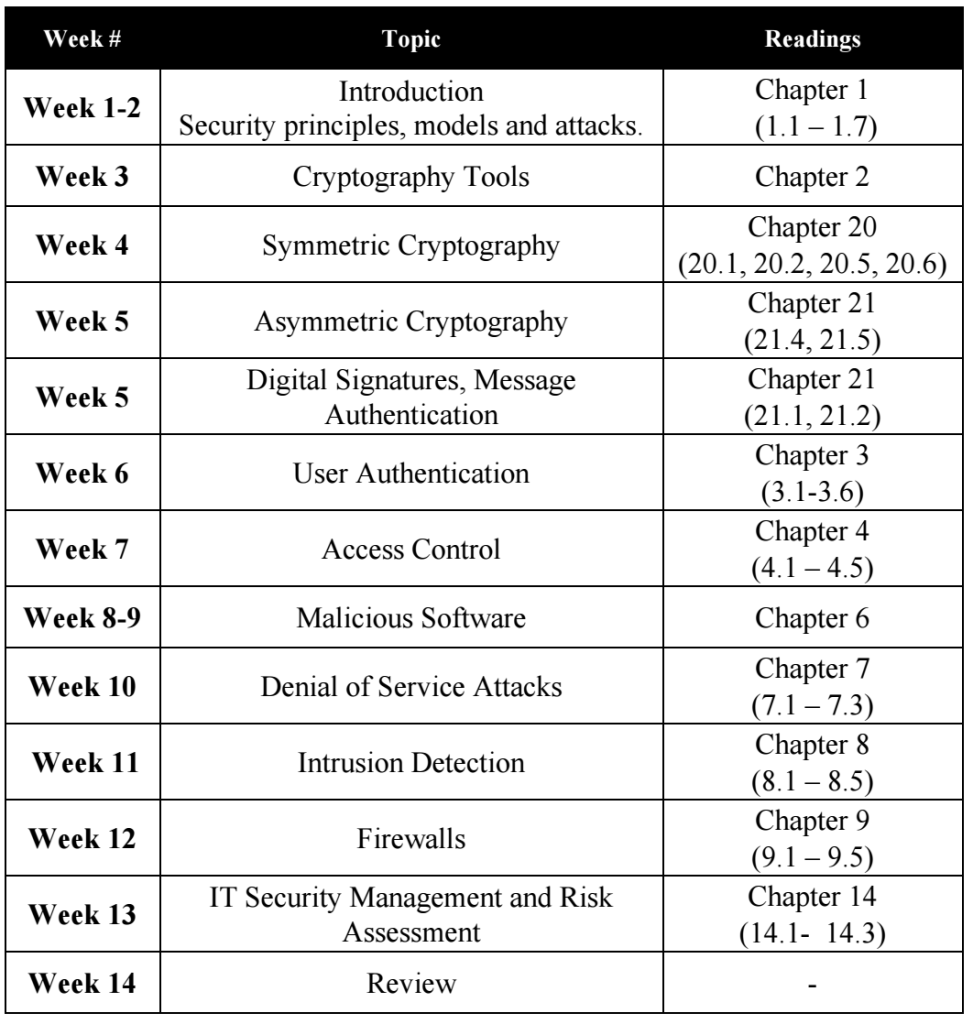
Course Schedule
14 weeks of three 50-minute lectures per week, in addition to 14 of 50-minute
tutorials.
Grading :
Assignments: 10
Project: 15
Quizzes: 10
Midterm: 25
Final: 40
Assignments :
- You have to post one question and its answer on the course website after every lecture. Also, you are required to evaluate someone else’s posted question and its answer from the previous lecture, giving score out of 5.
- All other assignments will be posted on LMS.
Course Learning Outcomes (CLOs)
The students will be able to:
1. Describe principles, requirements, and policies of computer security.
2. Recognize and differentiate the different types of security threats, attacks
and their implications.
3. Define and compare the various access control techniques.
4. Explain and analyze symmetric and asymmetric encryption algorithms and
their applications in digital signatures, and authentication.
5. Identify the major risk assessment approaches, techniques and tools used
to discover network, web, and system vulnerabilities and their
countermeasures.
6. Demonstrate ability to effectively communicate principles and policies of
security, and explain their applications in various contexts through class
presentation, assignments and course project.
Expected Performance Criteria
The students are expected to solve theoretical and practical questions in tutorials, programming project, pass midterm exam, and final exam based on class materials.
Course Policies
• Students who miss more than 25% of lectures will be denied from entering the final exam.
• No late assignments will be accepted.
• Plagiarism and cheating in exams, assignments or project are NOT tolerated and will results in receiving ZERO in the activity and may result in FAILING the course. In such event, King Saud University policies on plagiarism will be exercised.
• Submitting AI-generated content in assignments or project is considered plagiarism.

